NoScript Security Suite Giorgio Maone מאת
זמין ב־Firefox עבור ™Androidזמין ב־Firefox עבור ™Android
The best security you can get in a web browser! Allow potentially malicious web content to run only from sites you trust. Protect yourself against XSS other web security exploits.
יש צורך ב־Firefox כדי להשתמש בהרחבה זו
נתוני העל של ההרחבה
צילומי מסך
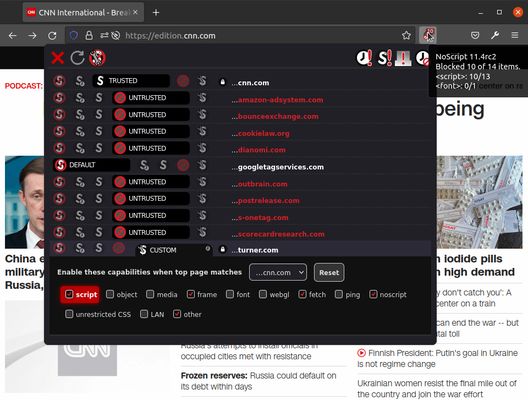
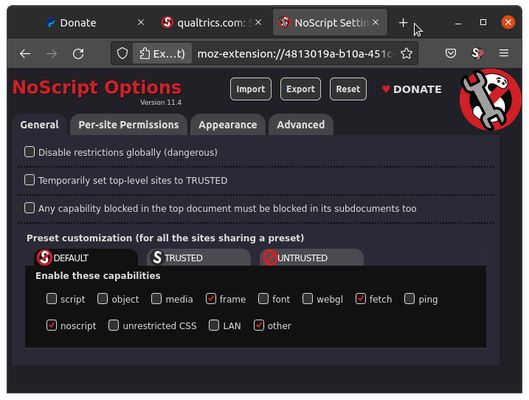
על אודות הרחבה זו
Winner of the "PC World - World Class Award" and bundled with the Tor Browser, NoScript gives you the best available protection on the web. It allows JavaScript, Flash, and other executable content to run only from trusted domains of your choice (e.g. your banking site), thus mitigating remotely exploitable vulnerabilities, such as Spectre and Meltdown.
It protects your "trust boundaries" against cross-site scripting attacks (XSS), cross-zone DNS rebinding / CSRF attacks (router hacking), and Clickjacking attempts, thanks to its unique ClearClick technology.
Such a preemptive approach prevents exploitation of security vulnerabilities (known and unknown!) with no loss of functionality where you need it.
Experts do agree: Firefox is really safer with NoScript!
FAQ: https://noscript.net/faq
Forum: https://noscript.net/forum
A Basic NoScript 10 Guide
Still confused by NoScript 10's new UI?
Check this user-contributed NoScript 10 primer.
and this NoScript 10 "Quantum" vs NoScript 5 "Classic" (or "Legacy") comparison.
It protects your "trust boundaries" against cross-site scripting attacks (XSS), cross-zone DNS rebinding / CSRF attacks (router hacking), and Clickjacking attempts, thanks to its unique ClearClick technology.
Such a preemptive approach prevents exploitation of security vulnerabilities (known and unknown!) with no loss of functionality where you need it.
Experts do agree: Firefox is really safer with NoScript!
FAQ: https://noscript.net/faq
Forum: https://noscript.net/forum
A Basic NoScript 10 Guide
Still confused by NoScript 10's new UI?
Check this user-contributed NoScript 10 primer.
and this NoScript 10 "Quantum" vs NoScript 5 "Classic" (or "Legacy") comparison.
הערות המפתח
Security issues affecting Firefox or the Tor Browser which can be fixed by a NoScript update are guaranteed to be addressed within 24 hours. This sometimes requires many updates to be issued in a short timespan, and when this happens you may notice NoScript UI's asking to "reload this page in order to operate properly". This is normal on "live" updates, and it just means the UI is out of sync with the page content, but there's no need to worry as all the restrictions to scripts and active content are still in place.
דירוג החוויה שלך
תמיכה במפתח זה
מפתח ההרחבה הזו מבקש ממך לסייע בהמשך הפיתוח על ידי מתן תרומה צנועה.
הרשאותמידע נוסף
תוספת זו זקוקה להרשאות הבאות:
- גישה ללשוניות
- אחסון נתונים בלתי מוגבלים של צד לקוח
- גישה לפעילות הדפדפן במהלך הניווט
- גישה לנתונים שלך מכל האתרים
מידע נוסף
- קישורים לתוספת
- גרסה
- 11.4.31
- גודל
- 932.54 ק״ב
- עדכון אחרון
- לפני 11 ימים (16 יולי 2024)
- קטגוריות קשורות
- רישיון
- GNU General Public License v2.0
- מדיניות פרטיות
- קריאת מדיניות הפרטיות עבור תוספת זו
- היסטוריית הגרסאות
- תגיות
הוספה לאוסף
הערות שחרור עבור 11.4.31
v 11.4.31
============================================================
x [L10n] Updated fr, is, ru, zh_CN
x Improved release tooling
x [nscl] Updated to latest NoScript Commons Library
x NoScript Options/Appearance/Show synthetic placeholders
for invisible capability probes (issue #369)
x [nscl] Make placeholders easier to style per type
x Prevent duplicate synthetic placeholders for invisible
capability probes (issue #369)
============================================================
x [L10n] Updated fr, is, ru, zh_CN
x Improved release tooling
x [nscl] Updated to latest NoScript Commons Library
x NoScript Options/Appearance/Show synthetic placeholders
for invisible capability probes (issue #369)
x [nscl] Make placeholders easier to style per type
x Prevent duplicate synthetic placeholders for invisible
capability probes (issue #369)
עוד הרחבות מאת Giorgio Maone
- אין דירוגים עדיין
- אין דירוגים עדיין
- אין דירוגים עדיין
- אין דירוגים עדיין
- אין דירוגים עדיין
- אין דירוגים עדיין